Critical VMware VMSA-2021-0020 | Runecast Analyzer
Yesterday (21 September 2021) VMware released a new VMware Security Advisory, VMSA-2021-0020, which was marked with a Critical severity rating. As with other recent VMSAs, VMware has included multiple CVEs with different severities into a single VMSA. Here we discuss the impact they may have on you and your infrastructure.
Common Vulnerabilities and Exposures (CVE) like this provide definitions for publicly disclosed cybersecurity vulnerabilities and exposures, and the VMSA provides VMware’s resolution and workaround information.
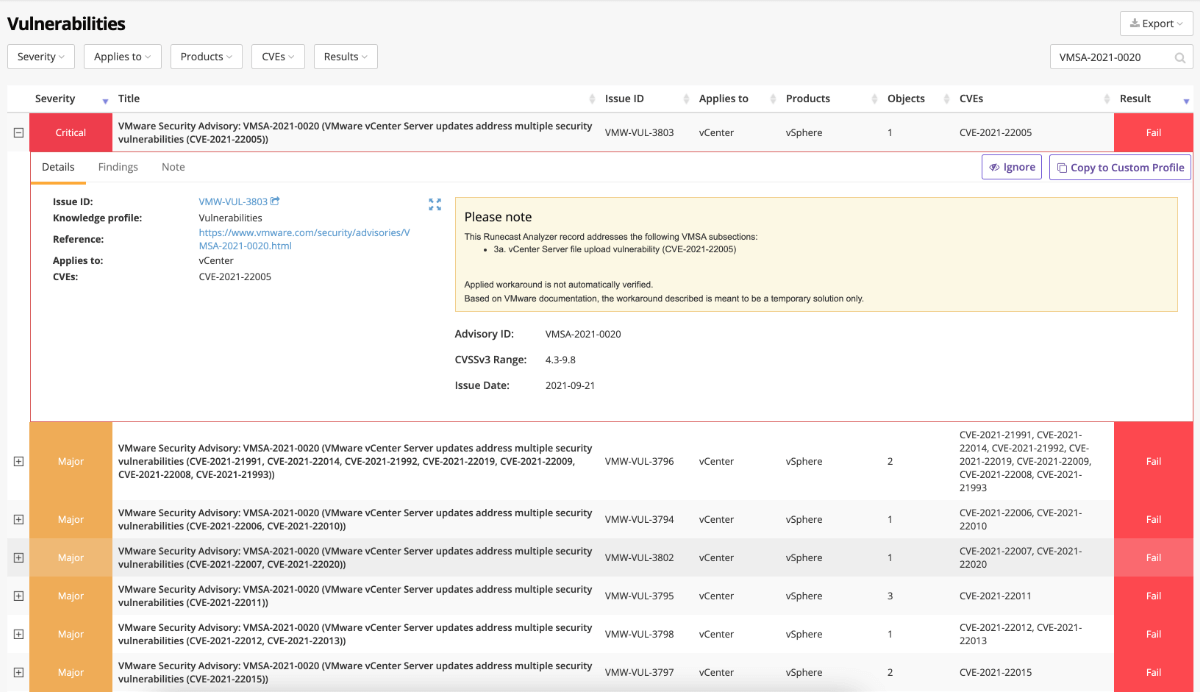
The Runecast Development team have split and grouped this VMSA and the 19 CVEs into 10 Runecast Analyzer records. This grouping helps to show the CVEs in logical groups, as several of the CVEs are fixed or remediated with the same solutions, allowing prioritisation of the highest severity issues. The records are based on severity, affected objects and required fixes – and are now available in the Runecast Analyzer v5.1.1.4 knowledge update. As always, where automatic updates are enabled, Runecast Analyzer users will receive the new definitions during the next update cycle, with offline updates available through the Runecast customer portal. This aligns with Runecast’s aim to provide coverage for all VMSAs within 24 hours of their release.
Below you can see screenshots of these CVEs being detected within Runecast Analyzer.
Summary
As these vulnerabilities all relate to the vCenter Server, we would recommend it is kept on a separate network, which is inaccessible from the internet.
We hope that these blog posts are helpful. Sometimes the abundance of technical information in a security advisory means that it can be hard to fully understand the impact that the vulnerabilities and the fixes might have on your environment, but we’re always happy to help.
The 19 CVEs and their resolution steps are covered in detail below.
vCenter Server file upload vulnerability (CVE-2021-22005)
VMware has evaluated the severity of this issue to be critical and has found an arbitrary file upload vulnerability in the Analytics service. In order to exploit this vulnerability, a malicious actor with access to port 443 on the vCenter Server would have to upload a specially made file, but they would then be able to execute code on the vCenter Server.
The fixed versions of vCenter Server (6.7 U3o, 7.0 U2c) are available for download. VCSA systems running version 7.0U2c build 18356314 which was released on August 24th are not vulnerable. This issue does not affect vCenter Server 6.5. Do note that the update is only necessary for VCenter Servers running 6.7 on Virtual Appliances, those running on Windows are not affected. VMware has also provided information on how to update vCenter Server on VMware Cloud foundation in KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7).
There is a workaround for this if you are not able to apply the update right away, as detailed in KB85717.
vCenter Server local privilege escalation vulnerability (CVE-2021-21991)
A local privilege escalation vulnerability has been identified in vCenter Server due to the way it handles session tokens. VMware has evaluated the severity of this issue to be important. A malicious actor with non-administrative user access could exploit this issue to escalate privileges to Administrator on the vSphere Client (HTML5) or vCenter Server vSphere Web Client (FLEX/Flash).
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. VMware has also provided information on how to update vCenter Server on VMware Cloud foundation in KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There is no workaround for this issue.
vCenter Server reverse proxy bypass vulnerability (CVE-2021-22006)
A reverse proxy bypass vulnerability has been discovered in vCenter Server due to the way the endpoints handle the URI. VMware has classified the severity of this issue to be important. A malicious actor with network access to port 443 on the vCenter Server could exploit this issue to access restricted endpoints.
The fixed versions of vCenter Server (6.7 U3o, 7.0 U2c) are available for download. This issue does not affect vCenter Server 6.5. VMware has also provided information on how to update vCenter Server on VMware Cloud foundation in KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There is no workaround for this issue.
vCenter server unauthenticated API endpoint vulnerability (CVE-2021-22011)
An unauthenticated API endpoint vulnerability has been discovered in vCenter Server Content Library. VMware has categorised this issue in the important severity range. A malicious actor with network access to port 443 on vCenter Server may exploit this issue to perform unauthenticated VM network setting manipulation.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There is no workaround for this issue.
vCenter Server improper permission local privilege escalation vulnerabilities (CVE-2021-22015)
vCenter Server contains multiple local privilege escalation vulnerabilities due to improper permissions of files and directories. VMware has categorised this issue’s severity as important. An authenticated local user with non-administrative privilege may exploit these issues to elevate their privileges to root level on vCenter Server Appliance.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). This update is only necessary for vCenter Servers running 6.7 on Virtual Appliances, those running on Windows are not affected. There is no workaround for this issue.
vCenter Server unauthenticated API information disclosure vulnerability (CVE-2021-22012)
There is an information disclosure vulnerability due to an unauthenticated appliance management API in vCenter Server. This issue affects only vCenter Server 6.5. A malicious actor with network access to port 443 on vCenter Server may exploit this issue to gain access to sensitive information. VMware has evaluated the severity of this issue to be important.
The fixed version of vCenter Server (6.5 U3q) is available for download. There is no workaround for this issue.
vCenter Server file path traversal vulnerability (CVE-2021-22013)
The vCenter Server contains a file path traversal vulnerability leading to information disclosure in the appliance management API. This issue affects only vCenter Server 6.5. A malicious actor with network access to port 443 on vCenter Server could exploit this issue to gain access to sensitive information.
The fixed version of vCenter Server (6.5 U3q) is available for download. There is no workaround for this issue.
vCenter Server reflected XSS vulnerability (CVE-2021-22016)
A reflected cross-site scripting vulnerability was discovered in vCenter Server 6.7, due to a lack of input sanitization. This issue affects only vCenter Server 6.7. VMware has evaluated the severity of this issue to be important. An attacker may exploit this issue to execute malicious scripts by tricking a victim into clicking a malicious link.
The fixed version of vCenter Server (6.7 U3o) is available for download. There is no workaround for this issue.
vCenter Server rhttpproxy bypass vulnerability (CVE-2021-22017)
rhttproxy as used in vCenter Server contains a vulnerability due to improper implementation of URI normalization. VMware has categorised the severity of this issue to be important. This vulnerability means a malicious actor with network access to port 443 on vCenter Server may exploit this issue to bypass a proxy leading to internal endpoints being accessed. This issue does not affect vCenter Server 7.0.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o) are available for download. There is no workaround for this issue.
vCenter Server authenticated code execution vulnerability (CVE-2021-22014)
An authenticated code execution vulnerability in VAMI (Virtual Appliance Management Infrastructure) has been discovered in vCenter Server. VMware classifies this issue’s severity as important. Due to this vulnerability an authenticated VAMI user with network access to port 5480 on vCenter Server could exploit this issue to execute code on the underlying operating system that hosts vCenter Server.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). This update is only necessary for VCenter Servers running 6.7 on Virtual Appliances, those running on Windows are not affected. There are no workarounds for this issue.
vCenter Server file deletion vulnerability (CVE-2021-22018)
An arbitrary file deletion vulnerability has been identified in a VMware vSphere Life-cycle Manager plug-in. This issue affects only vCenter Server 7.0. This vulnerability allows a malicious actor with network access to port 9087 on vCenter Server to delete non critical files.
The fixed version of vCenter Server (7.0 U2c) is available for download. There is no workaround for this issue. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB article KB85719. There are no workarounds for this issue.
vCenter Server XML parsing denial-of-service vulnerability (CVE-2021-21992)
The vCenter Server contains a denial-of-service vulnerability due to improper XML entity parsing. VMware has classed this issue as moderate severity. This would allow a malicious actor with non-administrative user access to the vCenter Server vSphere Client (HTML5) or Web Client (FLEX/Flash) to create a denial-of-service condition on the vCenter Server host.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There are no workarounds for this issue.
vCenter Server local information disclosure vulnerability (CVE-2021-22007)
The vCenter Server contains a local information disclosure vulnerability in the Analytics service. VMware has classed this issue as moderate severity. Exploiting this issue would give an authenticated user with non-administrative privilege the opportunity to gain access to sensitive information. This issue does not affect vCenter server 6.5.
The fixed versions of vCenter Server (6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There are no workarounds for this issue.
vCenter Server denial of service vulnerability (CVE-2021-22019)
There is a denial-of-service vulnerability in VAPI (vCenter API) service on vCenter Server. VMware has evaluated the severity of this issue to be moderate. A malicious actor with network access to port 5480 on vCenter Server may exploit this issue by sending a specially crafted jsonrpc message to create a denial of service condition.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There is no workaround for this issue.
vCenter Server VAPI multiple denial of service vulnerabilities (CVE-2021-22009)
Multiple denial-of-service vulnerabilities were identified in VAPI (vCenter API) service in vCenter Server. Due to these a malicious actor with network access to port 443 on vCenter Server may exploit these issues to create a denial of service condition due to excessive memory consumption by VAPI service.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There is no workaround for this issue.
vCenter Server VPXD denial of service vulnerability (CVE-2021-22010)
The vCenter Server contains a denial-of-service vulnerability in the VPXD (Virtual Provisioning X Daemon) service. VMware classifies this as a moderate severity issue. Due to excessive memory consumption by VPXD service a malicious actor with network access to port 443 on vCenter Server may exploit this issue to create a denial of service condition. This issue does not affect vCenter server 6.5.
The fixed versions of vCenter Server (6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). There are no workarounds for this issue.
vCenter Server information disclosure vulnerability (CVE-2021-22008)
The vCenter Server contains an information disclosure vulnerability in VAPI (vCenter API) service. A malicious actor with network access to port 443 on vCenter Server may exploit this issue by sending a specially crafted jsonrpc message to gain access to sensitive information. VMware has evaluated the severity of this issue to be in the Moderate severity range.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). Currently there are no workarounds for this issue.
vCenter Server Analytics service denial-of-service Vulnerability (CVE-2021-22020)
There is a denial-of-service vulnerability in the Analytics service of vCenter Server. Successful exploitation of this issue may allow an attacker to create a denial-of-service condition on vCenter Server. However, this issue does not affect vCenter Server 6.5.
The fixed versions of vCenter Server (6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). At this time there are no workarounds for this issue.
vCenter Server SSRF vulnerability (CVE-2021-21993)
Due to an improper validation of URLs in vCenter Server Content Library the vCenter Server contains an SSRF (Server Side Request Forgery) vulnerability. An authorised user with access to the content library may exploit this issue by sending a POST request to vCenter Server which could lead to information disclosure.
The fixed versions of vCenter Server (6.5 U3q, 6.7 U3o, 7.0 U2c) are available for download. A guide on how to update vCenter Server on VMware Cloud foundation is found in the KB articles KB85719 (vSphere 6.7) and KB85719 (vSphere 7). Currently there are no workarounds for this issue.